- The first open burpsuite tools, this tools there are on Backtrack.
- Then open dvwa on browser with entered address 192.168.56.1
select DVWA
See on burpsuite
burpsuite shows cookies from dvwa, this needed for options sqlmap
- open sqlmap, then open sql injection to show databases from dvwa
See on above, there are more options that you can used
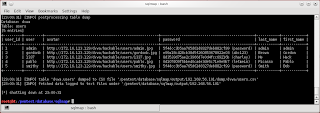
- Start view databases
- Then view tables dvwa
- Then view content on 'users'
up here, we was found the list of users from databases. But, this only users for login on dvwa. In here I'm trying to getting rootshell (SSH).
- Using File Inclusion
open dvwa on browser, then on tab address add syntax
in the back like below :
See what happen ?
There many users are showed, but we dont know the password.
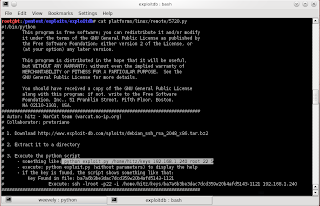
Next step is search vulnerabillty of ssh on exploit-db
Then show the options from the file
Then execute, in here I try the user 'root'
But.. it failed to found the encrypted password.
Now, I will trying use silent backdoor with weevly. You can see the explanation
here.
Lets try..
- Generate first the backdoor like below :
- Then open DVWA and select upload button then browse the file, before add the file to upload, we must rename the file and add extension .jpg in the end of name.
And click upload.
- Now open the burp suite and see what's are showing by burpsuite
- The next is trying connection with command like below
Then..
But, this not rot shell :(
Now I will trying gaining the root with exploiting the kernel
Check the kernel first
Afterthat search the exploit
Then download the exploit on
exploit-db and save on /var/www
Now download the file exploit from system target (dvwa system)
Next , please compile the file exploit so that can be executed
If done, create script on /tmp/tun to make the target connecting to our system
Now run netcat from our system and make listening via port 1234
Afterthat run exploit on system target
Ups.. it failed, oooh I forget do not add the PID
Check the PID
Now run again the exploit with add the PID like command below
#./exploit 2287
Back to our terminal and and look what happened there
Succes, Now we was on root shell :D